Tag: Network Security

Proxy Testing and Verification: Navigating the Complexities
In an era where data privacy and security are paramount, the use of proxies has...

Understanding TLS/SSL Proxy Errors: A Comprehensive Guide
In the digital landscape, secure communications are paramount. TLS (Transport Layer Security) and SSL (Secure...

Understanding Proxy Disconnection Issues: A Technical Guide
Proxy servers have become indispensable in today's digital landscape, serving as intermediaries that facilitate secure...

Understanding WebRTC Leaks and Proxy Issues
WebRTC (Web Real-Time Communication) has revolutionized the way we conduct peer-to-peer communications over the web....
How Do Proxy Servers Work?
How Do Proxy Servers Work? In the vast digital landscape we traverse daily, where information...
Geolocation of Proxy Servers
In the vast expanse of the digital age, a peculiar phenomenon exists—a realm where your...
Reverse DNS Lookup
In the vast realm of the internet, where data flows like a mighty river and...
TLS/SSL Encryption
Understanding TLS/SSL Encryption in the Context of Proxy Usage In the vast, intricate web of...
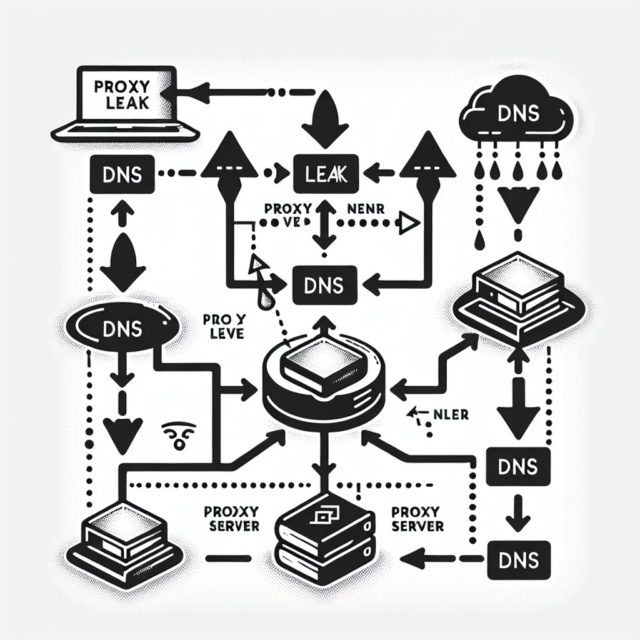
DNS Leak
What is DNS Leak? A DNS leak occurs when your internet traffic, specifically the Domain...
Firewall
What is a Firewall? A firewall is a security system that monitors and controls incoming...

TLS Handshake Failed – How to Fix Proxy SSL Errors
Transport Layer Security (TLS) is a critical protocol for ensuring secure communication over the internet....

TLS Handshake Failed – How to Fix Proxy SSL Errors
Transport Layer Security (TLS) is a vital protocol that secures communications over a computer network....

Understanding Proxy Authentication Issues: Error 407 vs Error 511
Proxy authentication errors can present significant challenges for network administrators and developers alike. Among these...