Blog

Multilogin или Incogniton — что выбрать для антидетекта?
Обзор софта: Multilogin vs. Incogniton для антидетекта В мире цифрового маркетинга и онлайн-бизнеса необходимость анонимности...
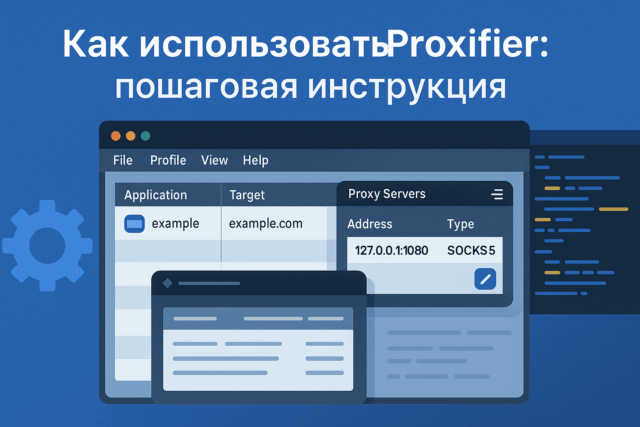
Обзор Proxifier: Пошаговая инструкция по использованию
Proxifier — это мощный инструмент для работы с прокси-серверами, позволяющий перенаправлять интернет-трафик любых приложений через...

Тестирование NetNut — стоит ли своих денег?
Тестирование NetNut — стоит ли своих денег? В мире прокси-сервисов, где каждый второй стартап обещает...

Proxy-Seller против IPRoyal: что выбрать?
Proxy-Seller против IPRoyal: что выбрать? В мире, где цифровая приватность и автоматизация становятся не просто...

Обзор лучших программ для прокси-чекеров
В мире интернет-технологий, где анонимность и безопасность становятся все более актуальными, прокси-серверы стали незаменимыми инструментами....
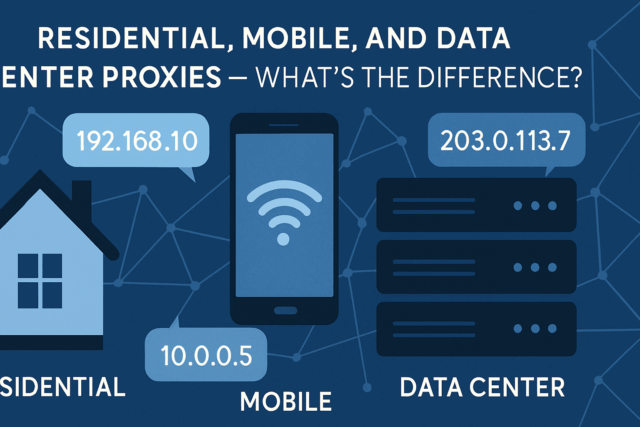
Резидентные, мобильные и дата-центр прокси — в чём отличие?
В современном интернете прокси-серверы — неотъемлемый инструмент для анонимности, парсинга, обхода блокировок и автоматизации. Но...

Разница между HTTP, HTTPS, SOCKS5 и другими типами прокси
В мире Интернета, полном цифровых переулков и закоулков, прокси-серверы играют роль своеобразных «швейцарских ножей» —...

Обзор лучших прокси-сервисов 2025 года
Обзор лучших прокси-сервисов 2025 года В эпоху цифровых барьеров и возрастающей ценности приватности прокси-сервисы стали...
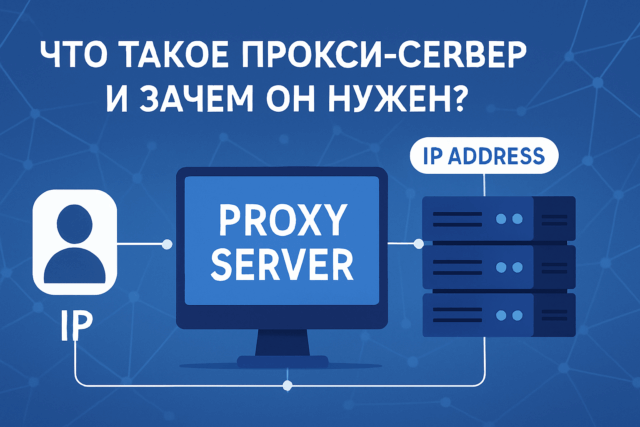
Что такое прокси-сервер и зачем он нужен?
В мире интернета прокси-серверы — это нечто вроде вежливого секретаря, который принимает ваши письма, пересылает...